All About Skimming
A General Knowledge Base
What is ATM Card Skimming?
Skimming is a technique used by criminals to copy personal data from the magnetic strip on an ATM card.
EAST (European ATM Security Team) defines Card skimming as;
“The card details and PIN are captured at the ATM and used to produce counterfeit cards for subsequent fraudulent cash withdrawals. The customer sees a normal transaction and retains the card. Multiple cards are compromised in one attack at one ATM.”
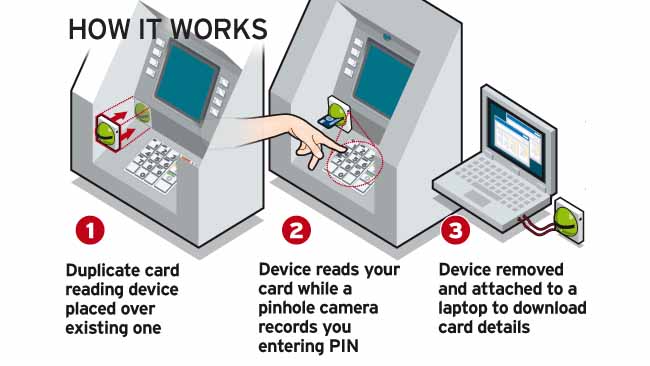
Typically fraudsters install a skimming device on top of the card slot of the ATM/SST, e.g. card reader cover, false front or pre-head; when a card holder inserts a debit or credit card, having a magnetic strip on the back, into the card reader, the skimming device will read the card details from the Track 2 of the magnetic stripand transmit these to a receiver connected either by wire or wireless.
Generally, a skimming device is accompanied with a PIN capturing device. This device is sometimes be a false pinpad or mostly a camera (or an other imaging equipment) strategially positioned on the fascia.

Facts On Skimming Devices?
– Skimming devices are normally attached to ATMs during quiet periods, e.g. early morning / late evening,
– Length of time skimming devices are attached can vary, but normally no longer than 24 hours,
– Successful skimming requires both a card skimmer (card reader) & camera (PIN capturing device) to be fitted to the ATM in order to steal card data,
– Criminals may loiter nearby to observe customers & remove equipment after machine use,
– Downloaded information can be transmitted wirelessly to other devices.
– Besides ATMs, other self service terminals (e.g. kiosks), retail cash registers w/card read head and gas pump stations are the other targets.
Smart Advices: Before You Use an ATM
Look Around Before You Approach
Take a quick look at your surroundings. See if anybody or anything looks suspicious. Is anybody watching you or standing too close? They might be looking for somebody who’s got cash (or is about to have cash very soon).
Use ATMs That You’re Familiar With
If you know an area well and have used an ATM before, you can expect similar results. In other words, your chances of getting robbed at a ‘familiar’ ATM are less than your chances of getting robbed at a ‘new’ ATM. There are a variety of reasons for this, but the point to stick with a trusted source.
Look Over the Machine Before Inserting Your Card
If you see something that looks unfamiliar or non-standard on the machine, it could be part of an ATM scam. Card skimmers (external readers) and hidden cameras can be used to compromise a bank account. Bottom line: if it looks funny, look for another ATM.
Always Secure Your PIN
Always use your hand to shield your PIN when entering it.
Have Your Card Ready While Approaching the ATM?
If you’re quick, your chances are better. On the other hand, you’re exposing yourself unnecessarily if you stand around the ATM digging through your wallet or purse for that special card. Get it out before you leave your car or as you’re approaching the ATM and get your transaction started as soon as possible.
Use ATMs That are Well Lit and Safe
Have you ever had to swipe your ATM (or Credit/Debit) card to get into an ATM booth after hours? One of the reasons is that only somebody with a valid card can get through the door. This makes it less likely that an ‘undesirable’ will approach you just as your cash is coming out. Obviously this is not foolproof — a crook can steal somebody’s card and use it immediately.
Check These Areas at an ATM for Any Suspicious Tampering:
1) Card reader entry slot,
2) Pinpad,
3) Illumination lightning area,
4) ATM Fascia sides

Avoid Using Your PIN Number at the Gas Pump.
When you pay at the pump with your debit/credit card, you usually have the option to use it as a credit or a debit card. It’s best to choose the credit option that allows you to avoid entering your PIN in sight of a Card Skimmer camera. Even if there is not a card skimmer camera in sight someone could be watching you enter your PIN and could subsequently mug you and take your card to the nearest ATM to withdraw some cash. When you use it as a credit card you usually only have to enter your billing ZIP code as verification which is much safer than putting in your PIN
Help the Legal Authorities
Report any unusual appearance immediately to Police or the nearest bank branch
Be vigilant! You can reduce the risk of skimming.
Latest Trends in Card Skimming and Preventive Policies
Card Skimming Trends for 2011
Payments card fraud is not expected to slow down anytime soon, especially from skimming attacks. Industry experts say card skimming at ATMs and points of sale is quickly reaching a tipping point in the United States, where lingering magnetic-stripe technology is making U.S. cardholders easy targets.
At the ATM card skimming remains the No. 1 fraud threat. But as distinguished Gartner analyst Avivah Litan points out, skimming at point of sale devices is becoming increasingly troublesome. “POS fraud is rising, and it’s likely because of skimming,” Litan says.
Skimming at ATMs has not changed much over the last decade. Most ATMs are compromised when skimming devices are placed over their external card readers. But technology advancements at the ATM have made strides to curb those skimming attacks. Still, while the ATM might is not necessarily the primary point of compromise, it is the channel used most often by fraudsters for fraud redemption — cash withdrawals.
Higher-Tech Schemes
One thing that is changing about skimming, regardless of where it’s perpetrated, is its increased sophistication and use of advanced technology. Across the board, fraudsters rely more on wireless communications to transmit skimmed card data. Bluetooth or cellular technology is the preferred wireless mode of communication, says Jeremy King, European regional director for the Payment Card Industry Security Standards Council. “Organized crime is getting more involved, and this is something we are watching closely,” King says. “Improving awareness is important, and the PCI PED standard is addressing some of the global card skimming trends we are seeing. In 2008, we added unattended terminals to the standard to address those trends.”
But the sophistication of organized crime goes deeper than technology, Gartner’s Litan says. The emergence of so-called “flash attacks,” which rely on coordinated, often international, efforts to simultaneously withdraw funds from multiple ATMs, is posing increased challenges for banks the world over.
Flash attacks, Litan says, “fly under the radar, because they involve several small withdrawal amounts that occur at the same time.” Institutions, already forced to cut budgetary spending for fraud detection, are fighting an uphill battle. “Banks can stop it if they can figure out the point of compromise, but many have a hard time doing that with current fraud-detection solutions,” she says.
A Need for Cardholder Authentication
Stronger cardholder authentication through contactless radio-frequency identification payments or contact chip technology such as EMV could solve the authentication dilemma. Even one-time pass codes embedded into plastic payments cards would be an improvement, Litan says. Second-factor transaction authentication will be a focus for all financial institutions in 2011, if it’s not already, says Chuck Somers, vice president of ATM security and systems for Diebold Inc., the world’s second-largest ATM manufacturer. “Anything beyond better authentication would involve changing the whole infrastructure,” Somers says. “The industry is trying to look forward to say, ‘If I add this solution to my arsenal, what is the likely attack that the criminals will come back with?’ They always come back with something; we just want to have as many steps in place to combat that comeback as we can.”
From a skimming perspective, authentication will become more critical in 2011, as targets and modes of attack change, Somers says. “I would expect more internal skimming, more malware, and PCI becoming more active to make sure appropriate levels of software are running on machines like pay-at-the-pump, which have proven vulnerable to those attacks.”
Biometrics, a second-factor authentication layer deployed in countries such as Japan and Brazil, is not likely to be an authentication mode the U.S. pursues, Somers says. “Whether it’s a biometric on its own or a biometric that’s part of a two-factor authentication, in a closed system, where that user is registered and they don’t use their cards outside that country, we’ve seen some very effective biometrics solutions,” he says. “But it’s only effective in those closed systems. The other effective authentication solution is chip, such as EMV.”
Mobile as a second layer of authentication is a more likely option for the U.S., Somers says. “We’ve done some experimentation with mobile and one-time passwords that are sent via text to the mobile phone. Those are the kinds of things we could see more of,” he says.
Improved analytical software will be a necessity to fill the security gap until the U.S. makes a decision on EMV or some other form of payment technology that does not rely on the magnetic stripe. “Even if we decide to move to EMV for authentication, it will take three to five years to make the change,” Litan says. “We need software-based authentication now, and there does seem to be more discussion about it than ever before.”
The problem, Litan says, is that U.S. payments space lacks a push for uniformity. “We’re not low on technology solutions,” she says. “We’re low on agreements and mandates to move toward making stronger cardholder authentication part of the experience.”
Card Fraud’s Global Impact
That lack of payments uniformity is having a global impact, says Lachlan Gunn, who heads up the European ATM Security Team Ltd., also known as EAST. The lingering mag-stripe in the U.S. is making cardholders in EMV-compliant countries vulnerable, he says. To support a global payments infrastructure, EMV-compliant countries have continued to issue cards that contain both the EMV chip and the mag stripe. With the lingering mag stripe, EMV cardholder data can still be skimmed. So fraudsters copy card data in Europe and then create fake mag stripe cards for use in the U.S.
“As of 2010, 95 percent of ATMs in Europe are now EMV compliant, and for a long time we had seen skimming incidents going down,” Gunn says. “But now we see incidents going back up. The bad guys know that chip and PIN/EMV is making skimming more difficult, so they go to where they can use the mag stripe. For your side of the pond, that should be disturbing.”
Of the EURO 150 million card-related fraud losses reported in Europe over the last year, EURO 119 million resulted from fraudulent transactions made in the U.S. “That’s an opening gap,” Gunn says.
Some European countries, such as Belgium, are taking stands to stop accepting mag stripe cards altogether, Gunn says. In January, Belgium will no longer accept mag stripe-based card transactions. “If a Belgium card is skimmed, then it’s useless outside the Single Euro Payments Area,” he says.
That move could either push the U.S. to EMV or seriously kink the global payments infrastructure. “The debate in Europe now is, ‘Do we allow mag stripe transactions to continue at all?'” Gunn says. “As a control, we are increasingly seeing chip-only cards appearing in Europe, and long term, chip-only cards could become more and more prevalent.”
Belgium’s initiative, Gunn says, could spur a domino effect among other SEPA countries. “If it works for Belgium, hypothetically, other countries will follow,” he says. “2011 will be a year that the increasing impact of chip and PIN is seen more globally, and it could be a year when people in the U.S. plan to change.”
Some Card Skimming Instances Around the World
Texas Police Department Informs!
A team of organized criminals is installing equipment on legitimate bank ATMs in at least two regions to steal both the ATM card number and the PIN. The team sits nearby in a car receiving the information transmitted wirelessly over weekends and evenings from equipment they install on the front of the ATM (see photos). If you see an attachment like this, do not use the ATM and report it immediately to the bank using the 800 number or phone on the front of the ATM.
The equipment used to capture your ATM card number and PIN is cleverly disguised to look like normal ATM equipment. A skimmer is mounted to the front of the normal ATM card slot that reads the ATM card number and transmits it to the criminals sitting in a nearby car.
At the same time, a wireless camera is disguised to look like a leaflet holder and is mounted in a position to view ATM PIN entries.
The thieves copy the cards and use the PIN numbers to withdraw thousands from many accounts in a very short time directly from the bank ATM.
Reference: Texas Police Department
July 16, 2013: Getting Skimpy With ATM Skimmers
Cybercrooks can be notoriously cheap, considering how much they typically get for nothing. I’m reminded of this when I occasionally stumble upon underground forum members trying to sell a used ATM skimmer: Very often, the sales thread devolves into a flame war over whether the fully-assembled ATM skimmer is really worth more than the sum of its parts. Such was the fate of an audio-based ATM skimmer put up for sale recently on a private crime forum. The seller, a Ukrainian, was trying to offload a relatively pro-grade skimmer powered by parts cannibalized from an MP3 player and a small spy camera. The seller set the price at $2,450, but made the mistake of describing the device’s various parts, all of which can be purchased inexpensively from a variety of online retailers. For example, he told forum members that the main component in the card skimmer as an MSR-605, which is a handheld magnetic stripe reader of the sort that you might find attached to a cash register/point-of-sale machine at a retail clothing store, for example. Card skimmer device made for Wincor/Nixdorf ATMs This ubiquitous device can be had for approximately $200 at a number of places online, including Newegg.com and Amazon.com. The seller went on to describe the inexpensive flash storage drive that was incorporated in his device, and the modified tiny video camera that was hidden on the underside of a fake fascia designed to be affixed to the top of the ATM and record victims entering their PINs. The image above shows the fake fascia as it appears from the side meant to be pointed toward the PIN pad. This sales thread goes on for several pages, and the seller — beset on all sides by fraudsters charging that skimmer set is grossly overpriced — begins lowering the price. “Go ahead and use the cheap Chinese skimmers and see how they work!” the seller retorted to hecklers on the forum. Reference: krebsonsecurity.com The MSR-605 components combined with a battery and flash drive. The red stuff is 3M double-sided tape.

It’s unclear from the sales thread whether this skimmer seller ever managed to attract a buyer. However, two young men in Russia were arrested earlier this year for using a skimming set that was remarkably similar to this model.

Cash Claws, Fake Fascias & Tampered Tickets
Credit and debit card skimmers aren’t just for ATMs anymore. According to European anti-fraud experts, innovative skimming devices are turning up on everything from train ticket kiosks to parking meters and a host of other unattended payment terminals.
Recently, at least five countries reported skimming attacks against railway or transport ticket machines, according to the European ATM Security Team (EAST), a not-for-profit organization that collects data on skimming attacks. Two countries reported skimming attacks at parking machines, and three countries had skimming incidents involving point-of-sale terminals. EAST notes that Bluetooth devices increasingly are being used to transit stolen card and PIN data wirelessly.
The organization also is tracking a skimming trend reported by three countries (mainly in Latin America) in which thieves are fabricating fake ATM fascias and placing them over genuine ATMs, like the one pictured below. After entering their PIN, cardholders see an ‘out-of-order’ message. EAST said the fake fascias include working screens so that this type of message can be displayed. The card details are compromised by a skimming device hidden inside the fake fascia, and the PINs are captured via the built-in keypad, which overlays the real keypad underneath.
EAST found that eight countries reported cash-trapping attacks at ATMs, with three of the eight nation’s reporting “significant increases” in this type of attack. The most common method of cash trapping used by crooks continues to involve what’s known as a “cash claw,” a device designed to be inserted into the cash dispense slot on an ATM and pry additional bills from the machine as it opens to dispense cash.

“Cash claws” designed to pry additional bills from an ATM’s cash dispensing slot. Source: EAST
The latest report from EAST continues to emphasize that most card fraud stemming from skimming incidents in Europe is in fact perpetrated outside of Europe, particularly in the United States, the Dominican Republic, Brazil, Mexico, Peru and Thailand.
EAST posits that a big reason for this trend is the broad adoption in Europe for a bank card security standard known as EMV (short for Europay, MasterCard and Visa), more commonly called “chip-and-PIN.” Most European banks have EMV-enabled cards, which include a secret algorithm embedded in a chip that encodes the card data, making it more difficult for fraudsters to clone the cards for use at EMV-compliant terminals. Because chip-and-PIN is not yet widely supported in the United States, skimmer scammers who steal card data from European ATM users tend to ship the stolen card data to buyers or co-conspirators in the United States, where the data is encoded onto fabricated cards and used to pull cash out of U.S. ATMs.
EAST notes that in ten European countries, one or more card issuers have now introduced some form of “geo-blocking,” by which payment cards are blocked for usage outside of designated EMV Chip liability shift areas. The organization found that issuers which have adopted such tactics continue to show a decline in skimming incidents and in skimming related losses.
Update, Mar. 31, 9:27 a.m.: A reader who services ATMs took issue with my description of the way these cash claws typically operate. He offered a different explanation: The claw is pushed into the dispenser by the thief. When a customer requests cash the cash becomes trapped in the claw and is not visible by the customer because its behind the cash shutter/slot. The machine reports a fault with dispensing and is unable to pull the cash back from the dispenser because the claw us trapping it. The thief returns when the victim leaves and forces the shutter open and pulls the claw and cash out. According to the ATM guy, this kind of attack can vary in how its performed. For example the shutter can be forced open first and the claw inserted.

Reference: krebsonsecurity.com

Skimming devices found at train ticket kiosks in Europe. Source: EAST

This fake ATM fascia includes a card skimmer and bogus PIN pad. Source: EAST






